18 Jul One Year Later, Phishers Still Go After German Automakers
Luring buyers to malicious sites
– Jonathan Zhang, CEO at Whois XML API
Walnut, Calif. – Jul. 18, 2021
Cyber attacks often begin with an email containing a malicious file, a link to a phishing website, a fake invoice, or a payment request. The recently discovered malware campaign targeting German automakers is no exception. The phishing emails were sent to people working in the automobile sector, often bearing subjects about vehicle purchases, and used domains that imitated those belonging to legitimate German car dealerships.
Several domains were identified as indicators of compromise (IoCs) in a report published by Checkpoint including autohous-lips[.]de, autohause-meissner[.]de, autohaus-schreoter[.]info, autohaus-landharr[.]de, autohaus-buschgbr[.]de, and 30+ others. We pivoted on these and were able to identify more than 1,200 possibly connected properties, a sample of which can be downloaded from our website.
Analysis of the DNS Artifacts
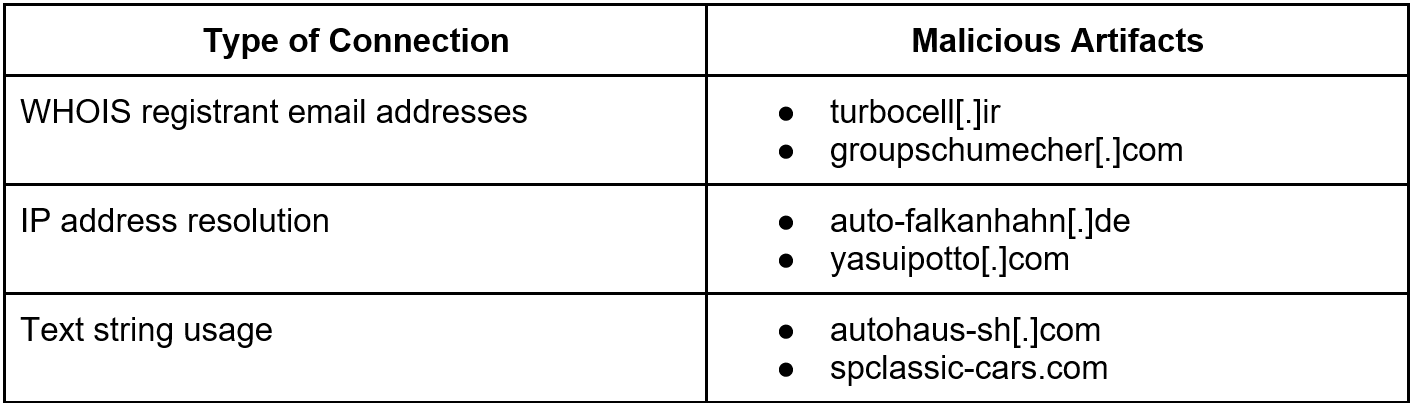
The identified artifacts shared one or several of the IoCs’ IP address resolutions, unredacted registrant email addresses, or the same text strings. Expanding the IoCs led us to 15 additional reported malicious properties.
Interestingly, we found malicious domains under each connection type (see Table 1), leading us to believe that all other artifacts have to be treated with suspicion. Even when some have not been flagged as malicious, it could only be a matter of time before they are weaponized. The table below shows some examples of malicious domains.
Table 1: Artifacts flagged as malicious for different connection types
Furthermore, some malicious properties still host content, including various registrant-connected domains like the below with indexed files.
On the other hand, the malicious domain auto-falkanhahn[.]de continues to host an active web page.
A screenshot analysis of all artifacts revealed that while several were parked, others hosted questionable content, including adult web pages. In particular, we found some domains — admin-shopify[.]com and inc-ialert[.]com — that hosted the same content as auto-falkanhahn[.]de.
Other domains also led directly to what seems to be login pages:
Screenshot of autohaus-kaessner-digital[.]de
Screenshot of ptautocarecenter[.]com
DNS Security Takeaways for the Automotive Industry
As threat actors continue to target automakers and their employees, customers, and other stakeholders, it might be worthwhile to:
- Continue screening newly registered domains (NRDs): Most of the IoCs in the German automaker-targeted campaign were newly added properties about a year ago. The domain autohous-lips[.]de, for example, appeared in the DNS in the first week of July 2021 and was used to send phishing emails shortly after.
- Pay attention to domain registrations containing industry-specific lexicons: Out of the 37 phishing IoCs examined, 25 contained either the text string “auto” or “car.” Dozens of the artifacts we uncovered through DNS connections also used these terms. Malicious actors cleverly use hyper-targeted text strings to increase the legitimacy of their web properties.
- Monitor branded cybersquatting domains: A study focusing on a cybersquatting campaign against the car manufacturing sector found thousands of digital properties bearing the names of top car companies, such as Toyota, Mazda, and Tesla, added in less than two months. Many of the domains have been flagged as malicious.
- Time is of the essence: Whether you are looking at cybersquatting domains, NRDs, or industry-targeted domains, threat actors may either immediately weaponize these properties or wait a while and progressively activate them. Regardless of the chosen approach, it can make a difference to be able to detect and monitor suspicious domain registrations in real-time, ideally well before they can cause any harm.
While looking out for threat, IoCs help prevent attacks that weaponize known malicious properties, expanding the list of IoCs by scrutinizing DNS and WHOIS connections can facilitate early threat detection. Some of the connected domains in this post, for instance, can be used to lure workers in the automobile industry or anyone interested in purchasing vehicles to malicious pages.
Feel free to contact us if you are interested in the IoCs and artifacts mentioned in this post or want to discuss research collaboration ideas.
– Jonathan Zhang is the founder and CEO of WhoisXML API—a domain and IP data intelligence provider that empowers all types of cybersecurity enterprises to build better products and achieve greater network security with the most comprehensive domain, IP, DNS, and cyber threat intelligence feeds. WhoisXML API also offers a variety of APIs, tools, and capabilities, including Threat Intelligence Platform (TIP) and Domain Research Suite (DRS).

Precise and exhaustive data is vital for cyber-security professionals to analyze and prevent cyber crime. Whois XML API offers a comprehensive collection of domain, WHOIS, DNS and threat intelligence data feeds that are essential to their work. It’s an exhaustive Cyber-security package that offers a maximum coverage of both real-time and historic data, complete with instruments for threat hunting, threat defense, cyber forensic analysis, fraud detection, brand protection, data intelligence enrichment across variety of SIEM, Orchestration, Automation and Threat Intelligence Platforms.