04 Feb As NFT’s Popularity Grows, So Does Cybersquatting
Tracking rogue domain names
– Jonathan Zhang, CEO at Whois XML API
Walnut, Calif. – Feb. 4, 2022
“If there’s a tweet, there’s a way,” seems to be the scammer mantra these days. Recently, Ozzy Osbourne shared a link on Twitter that turned out to be an NFT scam. It’s reminiscent of when scammers rode on Elon Musk’s tweets to lure crypto investors to what turned out to be scams. The enticement almost always points to a legit-looking website with a legit-sounding domain name.
As part of our DNS monitoring activity, we looked up NFT-related cyber resources to see if any of them could be vehicles for scams. We found more than 34,000 NFT-related domains and 32,000 subdomains as of mid-January 2022, which you may download here, along with other data points. Some of our significant findings include:
- Around 82 percent of the NRDs, including some malicious domains, actively resolved to 1,889 unique IP addresses.
- More than 200 domains containing the string “nft” could be cybersquatting on some of the largest brands and trademarks.
- Almost all cybersquatting domains cannot be publicly attributed to the imitated companies.
While these domains and subdomains could be meant for legitimate purposes, such as domain investing and launching a new business venture, we shouldn’t discount the possibility that some of them could be fronts for NFT scams.
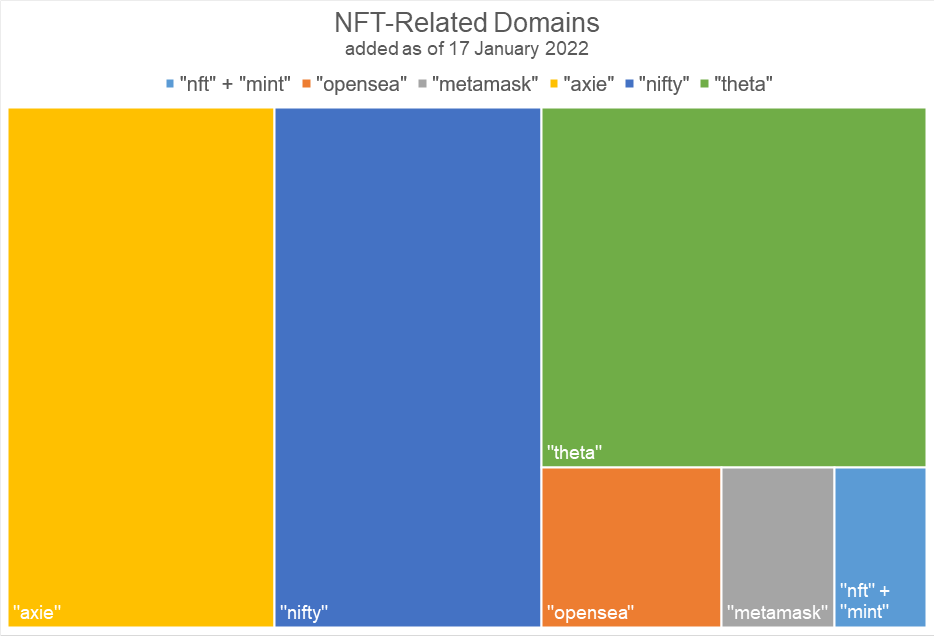
NFT Platforms and Tokens Seem Much Affected by Cybersquatting
Scammers tend to insert “nft” in domains, subdomains, URLs, email addresses, and other attack vectors to look more credible. They would also use other text strings related to NFT, such as “mint” and popular NFT platforms and tokens like OpenSea, MetaMask, Axie, and Nifty, to name a few. Famous names were used in more than 34,000 domains as per the breakdown below.
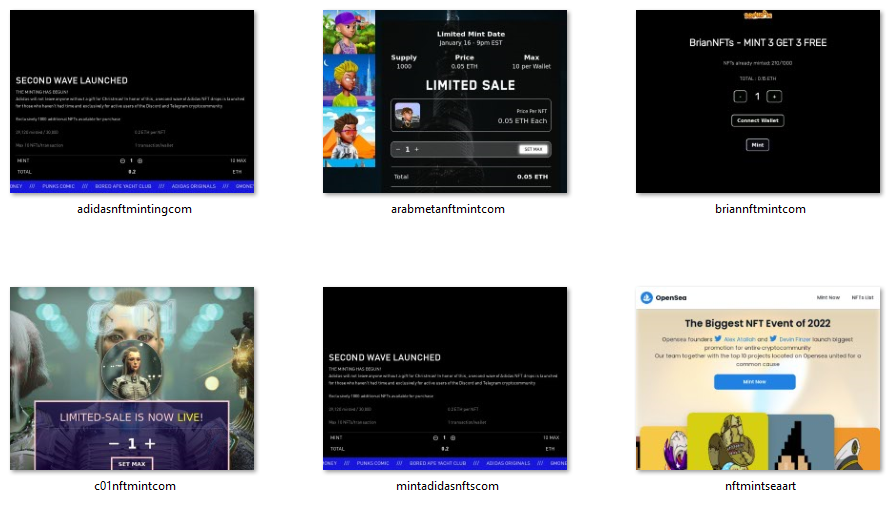
Some of these domains host NFT giveaways, limited offers, and other enticing content, such as the pages shown in the screenshots below.
They could either be legitimate or scam pages — we can’t know for sure unless victims start bleeding crypto. We did find 24 domains that have been flagged as malicious by various malware engines, including:
- cryptocatnftmint[.]art
- marketplaceaxieinfiniity[.]com
- marketplaceaxieonfinity[.]net
- metamask[.]gs
- metamask-connect[.]org
- metamask-kyc-regulations[.]de
- mint-castlekidnft[.]com
- mobile-metamask[.]com
- nftdoublemint[.]com
- openseagift[.]com
Popular Brand Names Might Be Abused, Too
Cybersquatting has been plaguing multinational companies for years, as evidenced by the increasing number of Uniform Domain-Name Dispute-Resolution Policy (UDRP) cases annually. The popularity of NFTs seems to add to this problem. Cybersquatters register NFT domains related to large enterprises. You may have noticed a couple of “adidas” domains in the screenshot above — adidasnftminting[.]com and mintadidasnfts[.]com.
The WHOIS records of these domains do not match the WHOIS breadcrumbs of the legitimate Adidas domain. We say “breadcrumbs” because while privacy redaction has rendered the WHOIS information of adidas[.]com invisible, some traces can still be found with WHOIS history.
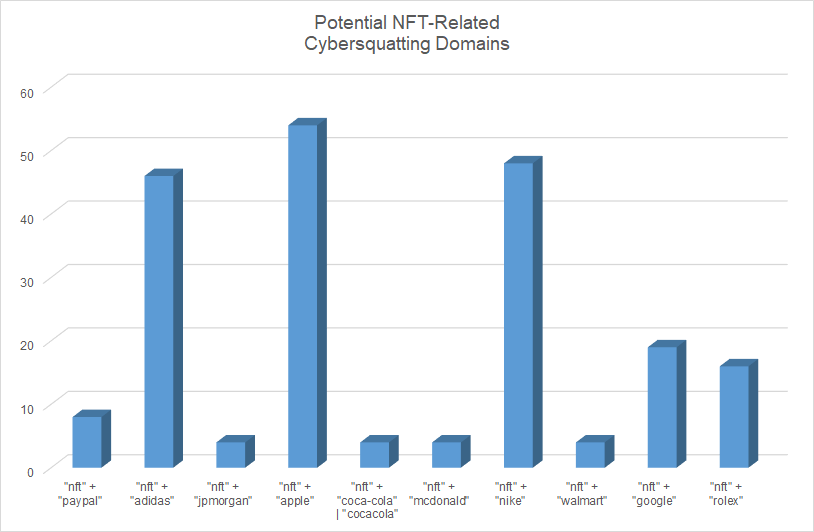
And, as it turns out, these domains are not the only ones. We detected more than 200 domains containing the string “nft” and brand names, such as PayPal, Adidas, JPMorgan, Apple, Coke, McDonald’s, Nike, Walmart, Google, and Rolex. A few examples include:
- paypalnft[.]io
- adidasnft[.]us
- jpmorgannft[.]com
- applenft[.]io
- nftcocacola[.]com
- nftmcdonald[.]com
- nikenfts[.]io
- walmartnft[.]art
- googlenft[.]com
- rolexnft[.]ch
These rogue domains have two potential implications. They can be used to victimize brand patrons looking into buying branded NFTs. On the other hand, brand owners could also find themselves filing UDRP cases to get a hold of these cybersquatting domains, similar to the experiences of WhatsApp and Comerica Bank.
We advise NFT enthusiasts to scrutinize tweets before clicking embedded links and investigate an NFT website before investing. More than anything, though, we want the cybersecurity community to be aware of these possible vehicles for NFT scams.
WhoisXML API’s WHOIS and DNS intelligence can uncover and attribute suspicious domains related to NFT and other mechanisms favored by scammers. Contact us for more information.
– Jonathan Zhang is the founder and CEO of WhoisXML API—a domain and IP data intelligence provider that empowers all types of cybersecurity enterprises to build better products and achieve greater network security with the most comprehensive domain, IP, DNS, and cyber threat intelligence feeds. WhoisXML API also offers a variety of APIs, tools, and capabilities, including Threat Intelligence Platform (TIP) and Domain Research Suite (DRS).

Precise and exhaustive data is vital for cyber-security professionals to analyze and prevent cyber crime. Whois XML API offers a comprehensive collection of domain, WHOIS, DNS and threat intelligence data feeds that are essential to their work. It’s an exhaustive Cyber-security package that offers a maximum coverage of both real-time and historic data, complete with instruments for threat hunting, threat defense, cyber forensic analysis, fraud detection, brand protection, data intelligence enrichment across variety of SIEM, Orchestration, Automation and Threat Intelligence Platforms.